I started working on this as soon as there was a reasonably easy way to detect vulnerable machines on Windows.
It includes:
- A script that you run against agents, which sets EDFs and highlights numerous things (BIOS/Firmware update, notes, whether certain mitigations are enabled and whether you are secure)
- A Dataview that you can import to have a good overview of all clients
- A Report that you can run to have something formatted to send to clients querying your action on this
- The underlying PowerShell I am using to populate the EDFs
A big thank you to Darren White for providing the Dataview.
If anyone wants to offer collective input, I will accept pull requests on the Github repos.
https://github.com/gavsto/Connectwise-Automate-Public-Scripts
Enjoy! The EDFs that get imported in “Meltdown and Spectre Detection” are seen below.
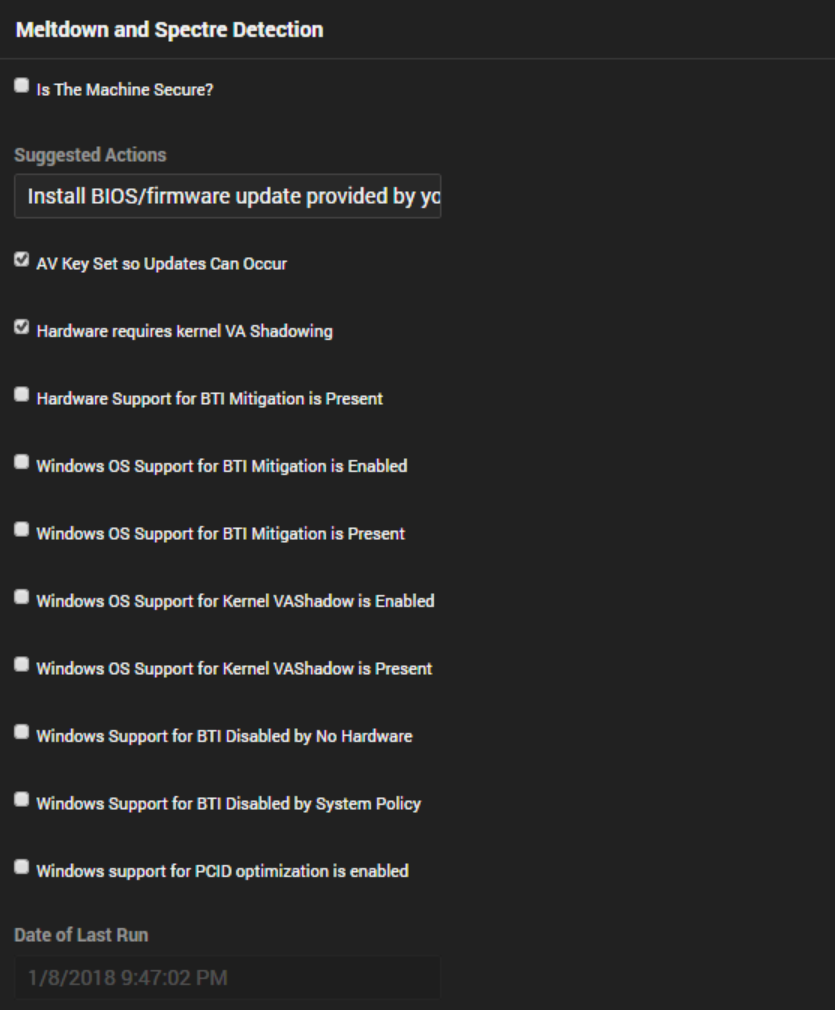


My AV provider is lazy (Webroot) to send out an update that would create necessary REG KEY that Microsoft is looking for prior to installing Spectre and Meltdown patches even though their current version is compatible with the patch. They said they will do it as part of new version which would not release until they are done with other feature enhancements possibly for another few weeks.
We are new to Labtech and are wondering if you could provide guidance on how to build a script that would create the right REG KEY on any computer we run the script on!
Thanks for all the great work you have done on this
Hi Tony.
See here: https://github.com/gavsto/ConnectWise-Automate-Meltdown-and-Spectre-Detection-Scripts/blob/master/Automate%20Scripts/Meltdown%20and%20Spectre%20-%20Set%20Allow%20Reg%20Key%20for%20Update.xml I’ve already included this in the solution
Just import that and run it against agents.
Just found this. Apparently this script creates it. Although it can be run from Webroot portal. It was provided by another end user (no thanks to Webroot support). How would I make a script for this in Labtech?
reg ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\QualityCompat /f /v cadca5fe-87d3-4b96-b7fb-a231484277cc /t REG_DWORD /d 0