Manual AV Magic
This post is aimed at people who are looking to detect anti-virus in a none standard way or are looking to detect Microsoft Defender for Endpoint using Automate.
Firstly, this is not as simple as just importing a virus definition for Automate. Because Defender for Endpoint is essentially an extension for Windows Defender, there doesn’t appear to be a single file that exists that definitively says “This agent has Defender for Endpoint on it”.
Step 1
The first step is to generate something locally (a file) that we can then detect using standard Automate AV Definitions, based on conditions we can script for. With Defender for Endpoint I know that two things are true when it is installed.
- The service called “sense” AKA “Windows Defender Advanced Threat Protection Service” is enabled and started; on machines with standard Windows Defender deployed this service is disabled
- A registry key exists in HKLM:\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status called OnboardingState, set to 1, that exists on machines with Defender for Endpoint on.
Based on this we can schedule a script to run (say daily) on all Automate machines that does the following:
$ServiceState = Get-Service sense -ErrorAction Stop
$OnboardingState = Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" -Name "OnboardingState" -ErrorAction SilentlyContinue
If (($ServiceState.Status -eq 'Running') -and ($OnboardingState.OnboardingState -eq '1'))
{
New-Item "C:\Windows\LTSvc\DefenderForEndpointPlaceholder.txt" -ItemType File -Force
}
else {
Remove-Item "C:\Windows\LTSvc\DefenderForEndpointPlaceholder.txt" -Force -ErrorAction SilentlyContinue
}This script creates a file called DefenderForEndpointPlaceholder.txt in a folder if the machine is Defender for Endpoint. If it isn’t detected, it deletes the file. We can then create a standard virus definition based on the creation of that file. You would need to put this in an Automate Script and schedule it to run (say daily) against all the endpoint you want to detect this on.
Step 2
If you do exactly that, then you can simply run this SQL insert command to add the final step in, which is an Automate AV detection template.
INSERT INTO `virusscanners` (`Name`,`DefLocation`,`DefFilename`,`ProgLocation`,`UpdateCMD`,`ScanTemplate`,`AutoProtect`,`OsType`,`VersionCheck`,`VersionMask`,`InfectionCheck`,`InfectionMatch`,`GUID`) Values('Microsoft Defender for Endpoint','{%-HKLM\\SOFTWARE\\Microsoft\\Windows Defender\\Signature Updates:SignatureLocation-%}\\mpasdlta.vdm','(.*)','C:\\Windows\\LTSvc\\DefenderForEndpointPlaceholder.txt','\"{%-HKLM\\SOFTWARE\\Microsoft\\Windows Defender:InstallLocation-%}\\mpcmdrun.exe\" -SignatureUpdate -Trace -Grouping 15 -GetFiles','','msmpeng*','1','','','','','8a83acb3-c897-4889-b58a-8f4a9dcdfc83');If you're hosted, save that string as a .SQL file and import it in System > General > Import > SQL File
If you’d prefer to add the Virus Scan definition yourself, go to Dashboard > Config > Configurations > Virus Scan
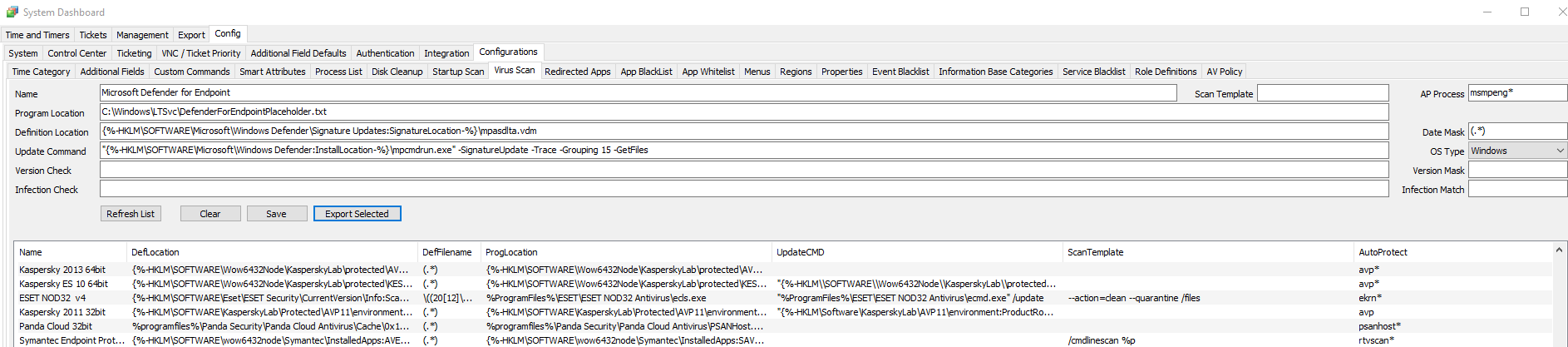
The values, for easy copy/paste:
Microsoft Defender for Endpoint
C:\Windows\LTSvc\DefenderForEndpointPlaceholder.txt
{%-HKLM\SOFTWARE\Microsoft\Windows Defender\Signature Updates:SignatureLocation-%}\mpasdlta.vdm
"{%-HKLM\SOFTWARE\Microsoft\Windows Defender:InstallLocation-%}\mpcmdrun.exe" -SignatureUpdate -Trace -Grouping 15 -GetFilesRemember – to properly detect the AV as a test, you need to run an Update Config THEN a Resend System Info. Bear in mind the thick client likes to lag and tell you AV is not installed unless you perform some voodoo magic and do a Reload System Cache. I personally just check in Automate Web as a simple F5 on the agent in the browser will tell you immediately.
Troubleshooting AV Detection
Confirm the configs.gz file under LTShare\Transfer folder has a timestamp newer than your last change. Use the Resend Config command Resend System Inventory command to perform AV detection and report the results. AV Product definitions that are detected on the agent are reported back, but only the lowest virusscanner.vscanid (Scanner ID, value in computers.virusscanner) is reported as the agent’s AV product. The Status\Antivirus Status Dataview can display the VirusScanner ID #. For an excellent article on how AV detection works in depth see Darren White’s post at https://forums.mspgeek.org/topic/4956-antivirus-tile-priority-manually-change/?tab=comments#comment-29012



Thanks for this Gav!
Question –
For an agent that runs Defender for Endpoint, with Huntress, I’m seeing the “sense” service is not disabled, but is set to Manual start, and is not running. The HuntressAgent service is running.
Do you know much about this scenario? Could I implement what you describe above, exactly as you write above with the exception of looking for the HuntressAgent service instead of the sense service?